Course Description
The only comprehensive course in the market that teaches absolute beginners Cyber Security GRC!
This course is video-based, with quizzes, practical assessments and a practical Capstone Project!
The concepts are taught in an easy-to-understand manner, with a focus on real-world applications and scenarios.
The course is fully practical. The instructor has condensed two decades of experience in this course. You will get to know the real problems that organisations face in the world of cyber security and how to solve them!
You don't need to cram multiple choice-based certification exams that don't teach you anything practical.
This course is the real deal.
Why Cyber Security GRC?
GRC is the cyber security specialisation that doesn't require any prior technical knowledge.
A lot of GRC roles are highly paid too AND a lot of these roles can be done remotely.
Starting your career in Cyber Security GRC is ideal for individuals with no prior technical experience.
Don't take my word for it!
See what our students are saying
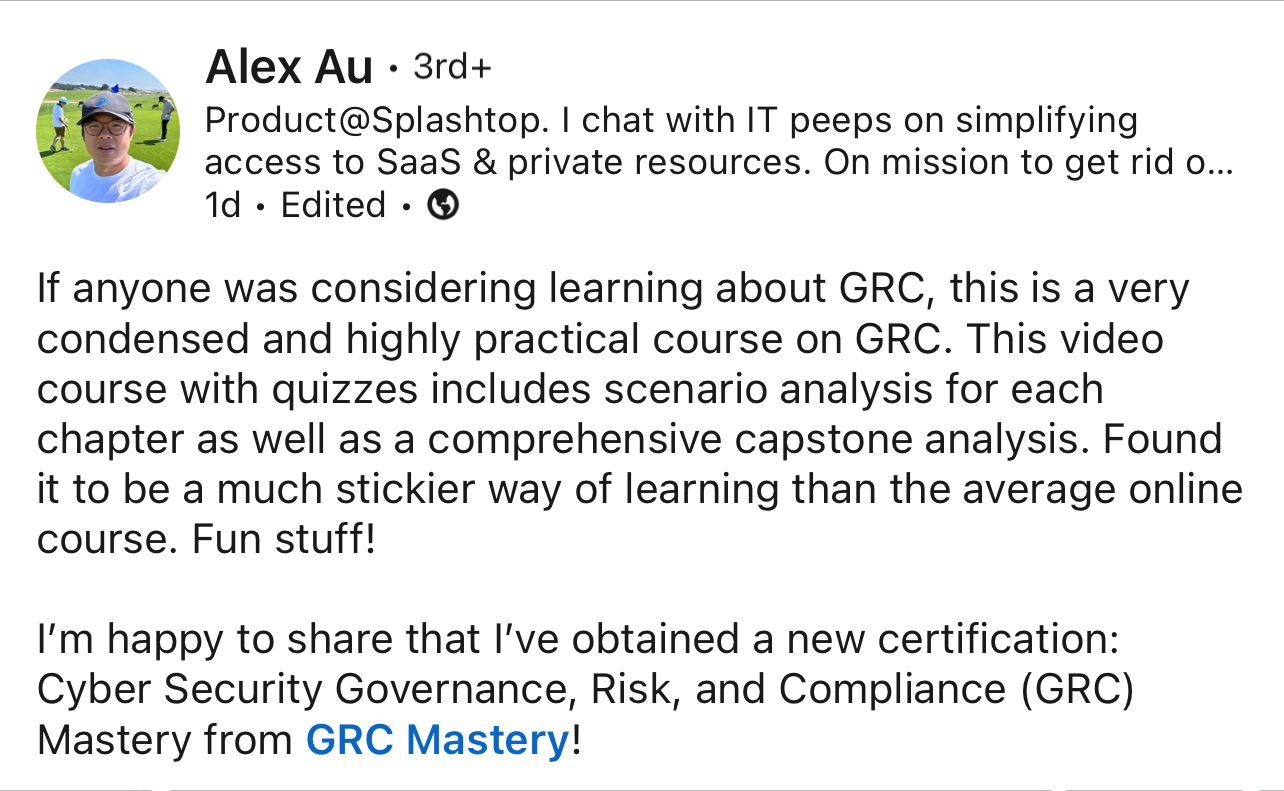
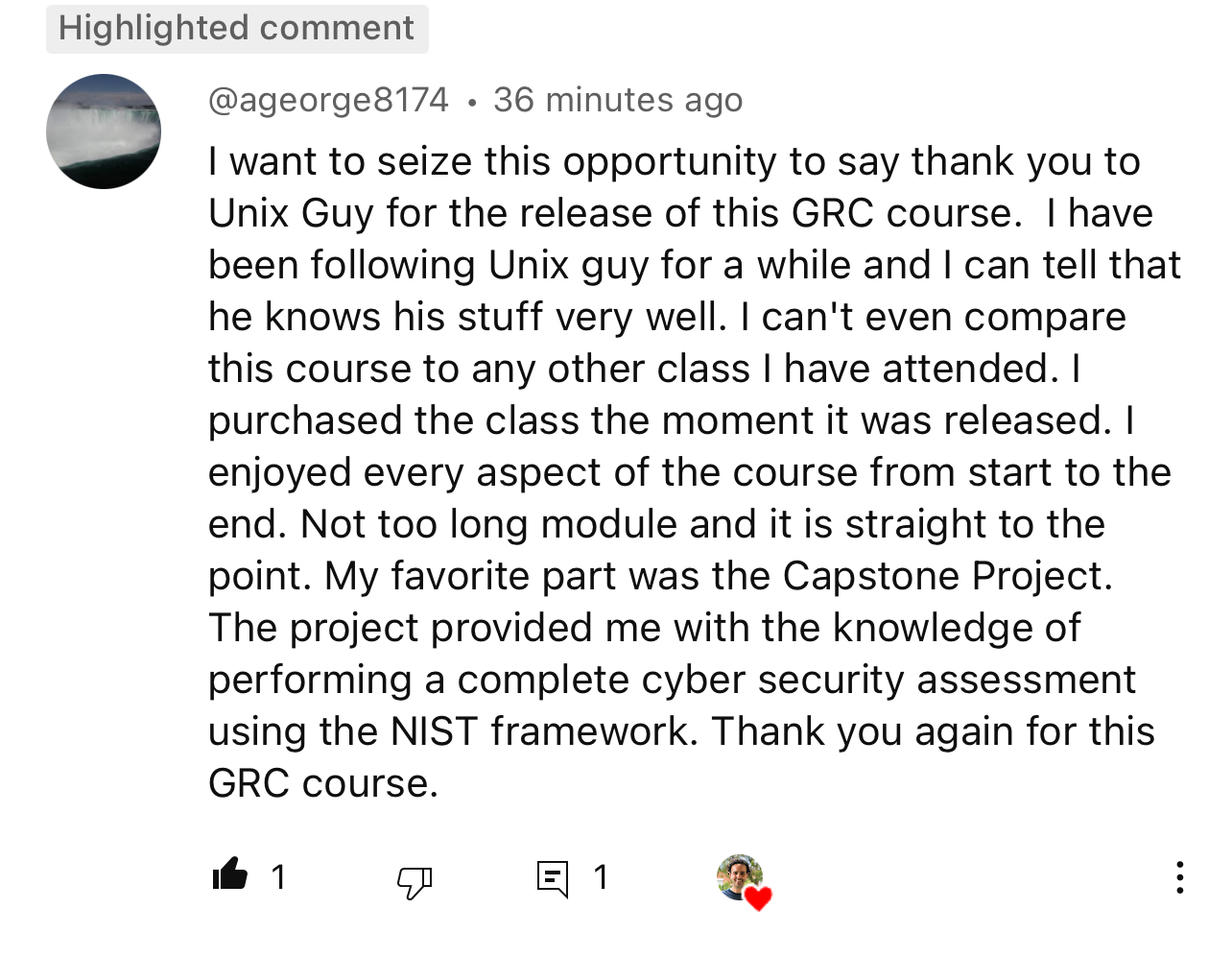
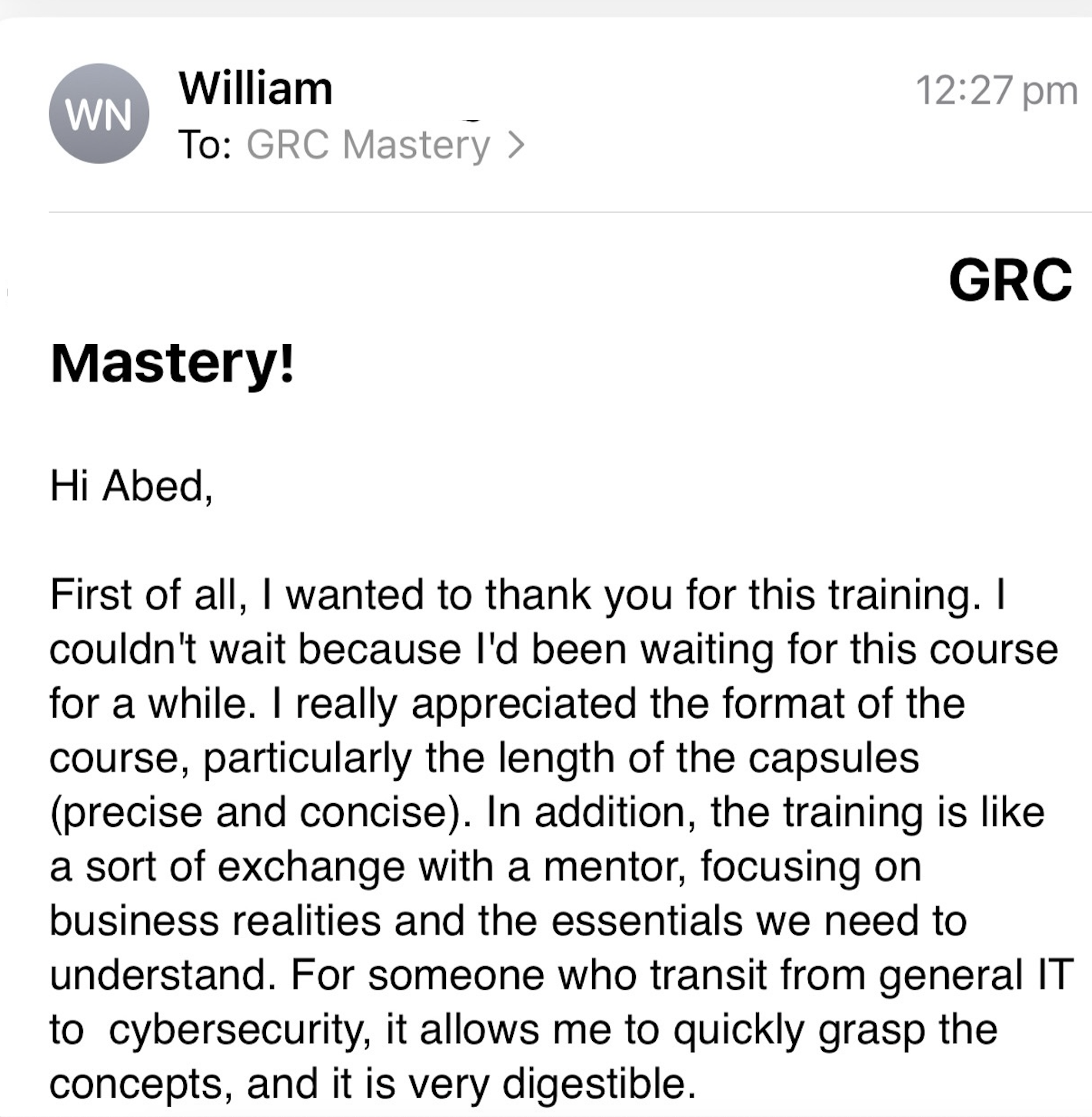
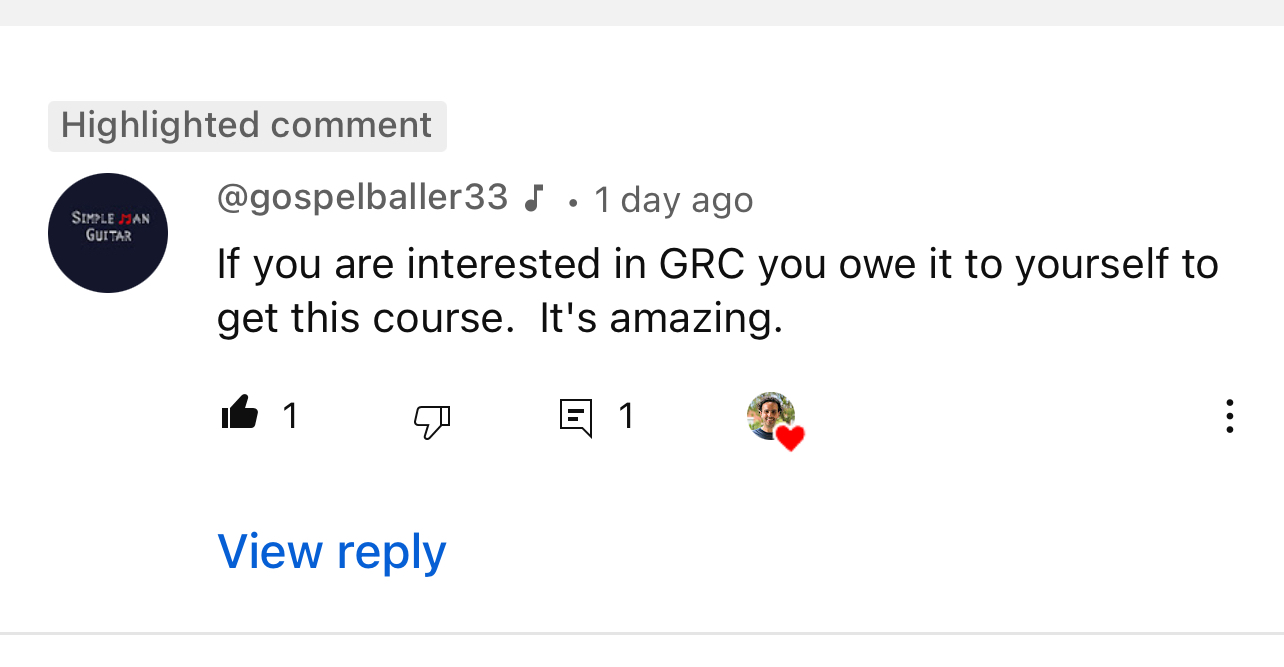

Meet your instructor
Abed has been working in the Cyber Security industry for over two decades. Started off as a Unix Guy securing Unix servers. He worked in different organisations and performed various cyber security roles. His most recent role is a Senior Manager at PwC Australia where he helps organisations with their strategic Cyber Security problems.
He mentored and helped hundreds of individuals from all over the world land their first cyber security job, which has become his main passion in recent years.
You can follow him on LinkedIn:
https://www.linkedin.com/in/abedhamdan/
Course Curriculum
- The real purpose of Cyber security risk management (3:17)
- Identify cyber security threats (2:04)
- Conduct cyber security risk assessments (2:32)
- Risk Registers (2:20)
- Cyber Security Frameworks (0:43)
- The CIA triad in the real world (1:51)
- The OWASP Secure Design Principles (8:14)
- The NIST Cyber Security Framework (1:52)
- Privacy Impact Assessments (PIA) (1:44)
- What most organisations get wrong about Cyber Security Risk (2:02)
- Knowledge Check
- Practical Assessment: CIA Triad
- Practical Assessment Solution: CIA Triad
- What is Asset Management? (0:48)
- Types of Assets
- Asset Identification (2:24)
- Asset Classification (3:18)
- CMDB (1:50)
- Why organisations fail at Asset Management (3:54)
- Practical approach to asset management (3:06)
- Knowledge Check
- Practical Assessment: Asset Management
- Practical Assessment Solution: Asset Management
- The role of IAM in Cyber Security (4:30)
- Authentication (2:09)
- Multi-Factor Authentication (MFA) (6:08)
- Managing passwords in the real world (4:14)
- Authorisation (4:20)
- Active Directory (4:34)
- Privilege Access Management (PAM) (4:35)
- Knowledge Check
- Practical Assessment: IAM
- Practical Assessment Solution: IAM
- The human element (1:52)
- Phishing (2:06)
- Social Engineering (3:40)
- Education and awareness programs (4:36)
- Measuring the effectiveness of Education and Awareness Programs (4:53)
- Problems with Education and Awareness in the real world (2:51)
- Knowledge Check
- Practical Assessment: Education and Awareness
- Practical Assessment Solution: Education and Awareness
- Detection and Monitoring (2:56)
- Security information and event management (SIEM) (6:04)
- Managed Security Service Provider (MSSP) (6:36)
- Cyber Security Incident Response (3:37)
- The MITRE ATT&CK framework (2:26)
- Cyber Drills and Crisis Simulation (4:15)
- The role of external service providers in incident response (1:52)
- Knowledge Check
- Practical Assessment: Incident Response
- Practical Assessment Solution: Incident Response
- What is this Third-party risk management (TPRM)? (4:13)
- The supplier discovery process (2:05)
- Supplier Classification (1:52)
- The supplier assessment process (2:01)
- The supplier assessment questionnaire (5:10)
- Issues with TPRM in the real world (5:21)
- Knowledge Check
- Practical Assessment: TPRM
- Practical Assessment Solution: TPRM
- What is Penetration Testing? (4:12)
- Types of Penetration tests (3:42)
- What organisations get wrong about Penetration Testing (4:52)
- What is vulnerability management? (3:42)
- Common problems in vulnerability management (8:48)
- Knowledge Check
- Practical Assessment: Vulnerability Management
- Practical Assessment Solution: Vulnerability Management
Frequently Asked Questions (FAQs)
Can I get a discount?
No, we can't give you preferential treatment. We kept the price fixed so it is fair to those who invested in the course. We priced the course a lot lower than its true value.
Are instalment plans available?
Yes, you can use Affirm, Afterpay, or Klarna. When you select "Card", those options will appear if they're available in your country.
What is GRC?
Governance, Risk, and Compliance (GRC) is the non-technical side of Cyber Security.
Does this course have any pre-requisites?
No, this course doesn't require you to have any technical background, or degrees or certifications.
Do we get lifetime access to the course when we purchase?
Yes, you get a lifetime access to the course when you purchase it.
Can you guarantee that I will get a job after doing this course?
That would be nice, but no. There is no course that can guarantee a job after. Some people will land a job straight after they finish this course. While others might take longer. It depends on how well you interview, how many jobs you apply to, job availability in your city, and many other factors that are outside of my control.
However, this course will give you all the skills and practice that you need to land a cyber security job. It even includes a bonus module designed to help you with the process of landing your first cyber security job.
Who is this course for?
For individuals who want to land a non-technical cyber security job. It's also suitable for technical individuals who want up-skill and learn GRC or cyber security professionals who want to progress into managerial roles or architecture but lack GRC skills.
Do I get a certificate when I finish this course?
Yes, you will get an official signed certificate when you finish this course. You can share it on your LinkedIn and on your resume/CV.
I'm technical, do I need this course?
This course will give you a holistic end-to-end view of cyber security programs. If you want to progress in your career and become a manager, then understanding GRC is a non-negotiable. This course will compliment your technical knowledge!
Can Cyber Security GRC professionals work remotely?
Yes they can. This will depend on the organisation. Some organisations allow 100% remote work while others use a hybrid work model with some days from home and some from the office. Other organisations don't allow remote work.
What kind of job can I get after finishing this course?
This training course prepares you for a career as a Cyber Security GRC professional. Jobs can include but are not limited to the following titles:
- Cyber Security GRC Analyst
- Information Security Analyst
- GRC Architect
- Cyber Security Architect
- Cyber Security Advisor
- Cyber Security Consultant
- Cyber Security Manager
- Cyber Security Risk Analyst
- Cyber Security Auditor
- Cyber Security Assessor
- Cyber Security Education and Awareness professional
- Cyber Security Analyst
- Third Party Security Assessment Analyst
- Technology Risk Analyst
- Technology Risk Partner
- Cyber Security Risk Partner
- Cyber Security Governance analyst
- DLP Analyst
- Data Loss Prevention Analyst
- Cyber Security Specialist
- Cyber Security Governance Specialist
- Cyber Security Risk Specialist
How long should this course take to complete?
It depends on how fast you go. Allow yourself at least one month.
The videos are intentionally short and to the point, but they contain a lot of information. You're meant to take notes, and I strongly recommend you watch the videos and do the course at least two times!
Give yourself a chance to absorb all the knowledge.
Can I get a refund?
No. We do not offer refunds due to the nature of this being a digital product and because we share the outline of all the course content before purchase.
Do you have an Affiliate program?
Yes we do. Click here to apply!
